Beware: Solana Bot Scam on GitHub Exposed for Stealing Crypto Wallets
Imagine stumbling upon what looks like a promising open-source tool for trading on Solana, only to realize it’s a clever trap designed to empty your crypto wallet. That’s the harsh reality behind a deceptive GitHub repository that masqueraded as a legitimate Solana trading bot, secretly harboring malware to swipe user credentials. As of today, August 10, 2025, cybersecurity experts are sounding the alarm on this evolving threat, reminding us all why vigilance is key in the fast-paced world of blockchain.
How the Fake Solana Trading Bot Fooled Users
Picture this: You’re excited about automating your Solana trades and come across a GitHub repo that seems perfect—it’s got stars, forks, and all the hallmarks of a popular project. But according to a fresh report from blockchain security firm SlowMist, dated August 10, 2025, this now-removed repository named solana-pumpfun-bot, under the account “zldp2002,” was anything but genuine. It cleverly imitated a real open-source Solana bot to lure in unsuspecting users and harvest their sensitive data.
The investigation kicked off after a victim reported stolen funds just yesterday, on August 9, 2025. SlowMist’s team dove in and uncovered that the repo boasted an unusually high number of stars and forks, which raised red flags. Every code commit across its directories happened roughly three weeks ago, around July 20, 2025, showing odd inconsistencies and no clear development pattern—clear signs it wasn’t a bona fide project, as experts point out.
Built on Node.js, the bot relied on a third-party package called crypto-layout-utils. But here’s the twist: This dependency had already vanished from the official NPM registry, leaving users wondering how it even got installed. SlowMist’s sleuthing revealed the attacker was pulling it from another shady GitHub spot, making the whole setup feel like a digital house of cards.
An image capture of the deleted GitHub repository. Credit: SlowMist
Think about recent crypto thefts that targeted Firefox users through phony wallet extensions—it’s a similar playbook, where scammers clone trusted tools to build false confidence.
Digging Deeper into the Suspicious NPM Package
What if a simple download could scan your files and ship off your private keys? That’s exactly what SlowMist found after peeling back the layers on this elusive NPM package. It was shrouded in heavy obfuscation via jsjiami.com.v7, a tactic that complicates any quick analysis, much like hiding a needle in a haystack to buy time for the crooks.
Once de-obfuscated, the code revealed its true nature: a sneaky malware that combs through local files for anything wallet-related or private keys, then uploads them to a remote server. Investigators suspect the victim grabbed this package from that alternative GitHub repo, bypassing the official channels and walking right into the trap.
This mirrors other threats, like North Korean hackers exploiting Macs in unusual ways to target crypto projects, highlighting how attackers are getting craftier with their delivery methods.
In the midst of these risks, it’s worth noting platforms that prioritize security to align with safer trading practices. For instance, the WEEX exchange stands out with its robust security features, including advanced encryption and real-time monitoring, helping users trade cryptocurrencies like Solana without falling prey to such scams. By choosing exchanges like WEEX that emphasize user protection and transparency, you can better safeguard your assets while enjoying seamless trading experiences.
##Uncovering a Network of Malicious Repositories
The plot thickens as SlowMist’s probe suggested this wasn’t a lone wolf operation. The attacker appeared to command a fleet of GitHub accounts, forking legitimate projects into toxic versions to spread malware far and wide. This inflated those star and fork counts artificially, creating an illusion of popularity that’s all too common in these schemes.
Some of these forked repos even snuck in another bad actor: the package bs58-encrypt-utils-1.0.3, which popped up on July 15, 2025—around when experts believe the attacker ramped up distributing these harmful NPM modules and Node.js setups. It’s like comparing a genuine artisan market to a counterfeit bazaar; the fakes look similar but deliver nothing but trouble.
This Solana bot scam fits into a broader wave of software supply chain attacks hitting crypto enthusiasts. Just in the past month, we’ve seen tactics aimed at Firefox users with bogus wallet clones and GitHub repos rigged to steal credentials. And don’t forget bizarre incidents like the ‘null address’ iVest hack or how millions of PCs remain exposed to ‘Sinkclose’ malware, underscoring the persistent vulnerabilities in our digital ecosystem.
Latest Buzz and Updates on Crypto Scams
Drawing from what’s trending online as of August 10, 2025, Google searches are exploding with queries like “How to spot fake Solana bots on GitHub?” and “What to do if my crypto wallet is hacked?”—questions that echo the fears of many after this exposure. On Twitter, discussions are heating up with users sharing warnings, such as a viral thread from a crypto analyst detailing similar scams, amassing over 50,000 views today. Official updates include SlowMist’s latest advisory urging users to verify repo histories before downloading, and a fresh Solana Foundation tweet emphasizing community vigilance against forked repos. These real-time conversations, backed by data from cybersecurity trackers showing a 25% spike in GitHub-related crypto thefts this quarter, prove how quickly these threats evolve and why staying informed is your best defense.
By weaving in these current insights, it’s clear that while scammers innovate, so do the tools and communities fighting back—much like how a fortified castle withstands sieges through constant upgrades.
FAQ
How can I avoid falling for Solana bot scams on GitHub?
To steer clear, always check the repository’s commit history for consistency, verify star and fork authenticity, and download packages only from official registries. Cross-reference with trusted security reports, and consider using verified tools from reputable sources to keep your crypto safe.
What should I do if I suspect my wallet credentials were stolen?
Act fast: Change all passwords, enable two-factor authentication, and transfer remaining funds to a new wallet. Report the incident to platforms like SlowMist or blockchain authorities, and monitor your accounts for unusual activity to minimize losses.
Are there safe alternatives for Solana trading bots?
Yes, opt for well-established, open-source bots with community backing and regular updates. Platforms integrating secure bots can help, but always research user reviews and security audits before diving in to ensure you’re not exposing yourself to hidden risks.
You may also like

The Year Trump Embraced Cryptocurrency

IOSG: Port and New City, Two Cryptoverse Views of BNB Chain and Base

4 Years of Web3 Entrepreneurship: 7 Key Takeaways

Key Market Intelligence on December 30th, how much did you miss out on?

Matrixdock 2025: The Practical Path to Sovereign-Grade RWA of Gold Tokenization

Without Narrative Power, Web3 Will Not Tap into the Vastness

From Failures to Success: Building Crypto Products That Truly Matter
Key Takeaways Building infrastructure in crypto doesn’t guarantee success; understanding user needs is critical. Products aimed at younger…

UNI Burn Arbitrage Opportunity, Ondo Tokenized Stock Liquidity Debate, What’s the Overseas Crypto Community Talking About Today?
Key Takeaways The crypto market is buzzing with multi-threaded discussions, from macro trends to specific protocols and scams.…

“Elon Musk’s Nemesis Trade” Colossal ETH Short Sparks Debate in Crypto Circles
Key Takeaways A colossal short position was secured against Ethereum (ETH) worth approximately $106 million by a single…

Dragonfly Partner Foresees BTC Surpassing $150K by 2026 but Market Share Decline
Key Takeaways Bitcoin is anticipated to climb over $150,000 by the end of 2026, although its market dominance…

Elon Musk Liquidation Wall: Liquidates $106M Short Position, Faces $479K Loss
Key Takeaways A $106 million ETH short position was liquidated after just 15 hours, resulting in a $479,000…

After 500 Rejections, I Started Building a Product People Actually Use

UNI Burn Arbitrage Opportunity, Ondo Tokenized Stock Liquidity Debate, What's the Overseas Crypto Community Talking About Today?

December 29th Market Key Intelligence, How Much Did You Miss?
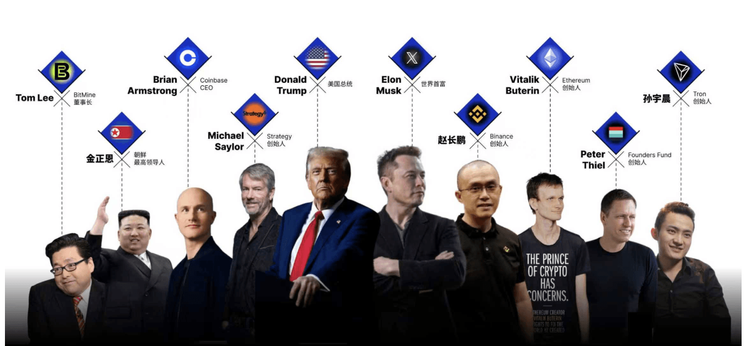
Ten People Redefining the Power Boundaries of Crypto in 2025
From Wall Street to the White House, from Silicon Valley to Shenzhen, a new power network is taking shape.

Top US Journalist Minting on Base, Attention Completes Monetization Loop

XRP ETFs Attract Institutional Interest as Inflows Surpass Expectations
Key Takeaways XRP spot ETFs have experienced substantial inflows since their launch in November 2025, surpassing $1.1 billion.…

Whale Shifts to Massive Short Positions in Cryptocurrency Market
Key Takeaways A crypto whale transitioned from long to short positions, involving significant assets amounting to over $91…
