50x Hyperliquid Whale Identity Revealed, Turns Out to Be a Fraudster Featured in UK News Headlines?
Original Author: ZachXBT, On-chain Detective
Original Translation: DeepSeek
Editor's Note: The article reveals the identity of a mysterious Hyperliquid whale involved in illicit activities, who made approximately $20 million in profit through high-leverage positions from January to March 2025. The investigation found that this individual exploited casino game vulnerabilities and phishing attacks to acquire funds, and conducted high-leverage trades on both Hyperliquid and GMX using multiple wallets. Ultimately, the whale was traced back to a connection with William Parker (formerly known as Alistair Packover), a convicted felon with a history of fraud and gambling crimes. Currently, the funds are primarily held in an Ethereum address.
The following is the original article content (rearranged for readability):
An investigation has revealed the identity of a mysterious Hyperliquid whale involved in illicit activities, who made approximately $20 million in profit through high-leverage positions over the past few weeks.
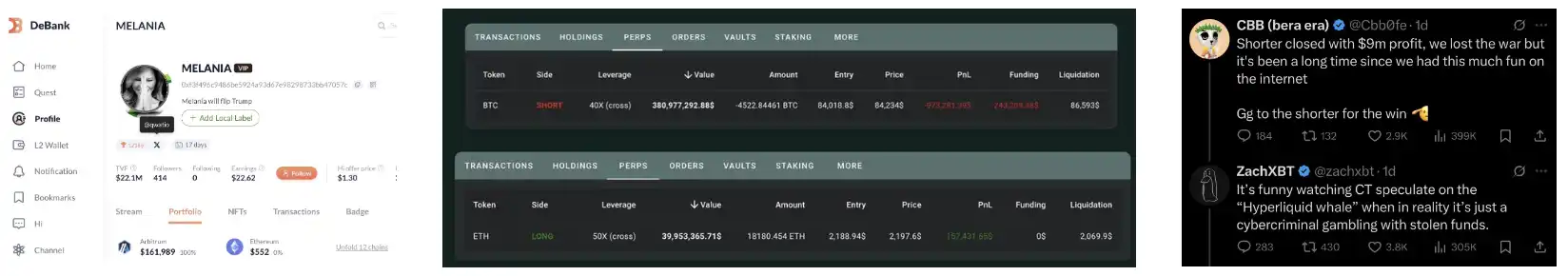
A trader opened multiple high-leverage positions on Hyperliquid and GMX from January to March 2025.
They drew widespread attention this month due to two on-chain transactions:
· Before Trump's announcement of a cryptocurrency reserve, 0xe4d3 opened a large ETH and BTC long position with 50x leverage (earning $10 million).
· 0xf3F4 opened a large BTC short position with 40x leverage (earning $9 million).

I further investigated and identified the primary counterpart of 0xf3f:
0x7ab8c59db7b959bb8c3481d5b9836dfbc939af21
0x312f8282f68e17e33b8edde9b52909a77c75d950
0xab3067c58811ade7aa17b58808db3b4c2e86f603
0xe4d31c2541a9ce596419879b1a46ffc7cd202c62
These addresses are associated with Roobet, Binance, Gamdom, ChangeNOW, Shuffle, Alphapo, BC Game, and Metawin accounts.

0xf3f for X account @qwatio signed a message and claimed to have made $20 million on GMX and HL.
This implies that he must control the wallets related to this cluster for the $20 million figure to be accurate.
I replied to him on X yesterday, but the post was subsequently deleted.

An analysis of the X account used by 0xf3f suggests that the account may have been purchased at some point in time (recent name change, long period of inactivity, relatively old account).
I noticed that they follow @CryptxxCatalyst, who has posted links to multiple phishing websites and has replied to some individuals, attempting to deceive them.

I contacted @realScamSniffer, who regularly tracks these phishing websites.
In January 2025, a public address of a Hyperliquid whale was set as the receiving address for the projection[.]fi phishing website.
0x7ab8c59db7b959bb8c3481d5b9836dfbc939af21
In January 2025, 0x7ab also directly received $17,100 from another phishing victim, and then his wallet was traced this month.

Since 0x7ab is the first EVM address used by 0xf3f, I traced the funds back to withdrawals from four casinos on Solana.
83Dumvk6pTUYjbGrC1fizBziRzDqcyNx73ieJcVbp56b
I contacted one of the casinos, and they clarified that the funds came from an input validation bug in their casino games.
They provided a now-deleted Telegram account: 7713976571, where they had negotiations with the exploiter of this bug.

I found a post from this account in a Telegram group through Open Source Intelligence (OSINT).
I discovered three help posts posted by the same TG ID in a GMX group.
To verify that this is the same person, I noticed that the posting times of these posts coincide with the on-chain transaction time of 0xe4d3.

I traced a recent payment by 0xe4d3 to an unnamed individual who confirmed they had been paid by an HL trader.
They provided a UK phone number for communication.
Public records indicate that this number is likely associated with the name William Parker.

Who is William Parker?
Last year, WP was arrested and sentenced in Finland for stealing approximately $1 million from two casinos in 2023.
Prior to this, WP was known as Alistair Packover (William Peckover) and later changed names.
In the early 2010s, AP made headlines in the UK news for fraud charges related to hackers and gambling (the age in the article matches the current information).

Clearly, WP/AP did not learn from their fraud conviction and is likely to continue gambling.
Currently, funds are primarily held in the following address:
0x51d99A4022a55CAd07a3c958F0600d8bb0B39921
Here is a quick summary:
In January 2025, an individual with a history of crimes leveraged a casino game vulnerability and phished victims, turning a six-figure sum of funds into $20 million through high-leverage on-chain transactions.
Popüler coinler
Güncel Kripto Haberleri
Müşteri Desteği:@weikecs
İş Birliği (İşletmeler):@weikecs
Uzman İşlemleri ve Piyasa Yapıcılar:bd@weex.com
VIP Hizmetler:support@weex.com
